Table of Contents
- 1. Executive Snapshot
- 2. Impact and Evidence
- 3. Technical Blueprint
- 4. Trust and Governance
- 5. Unique Capabilities
- 6. Adoption Pathways
- 7. Use Case Portfolio
- 8. Balanced Analysis
- 9. Transparent Pricing
- 10. Market Positioning
- 11. Leadership Profile
- 12. Community and Endorsements
- 13. Strategic Outlook
- Final Thoughts
1. Executive Snapshot
Core Offering Overview
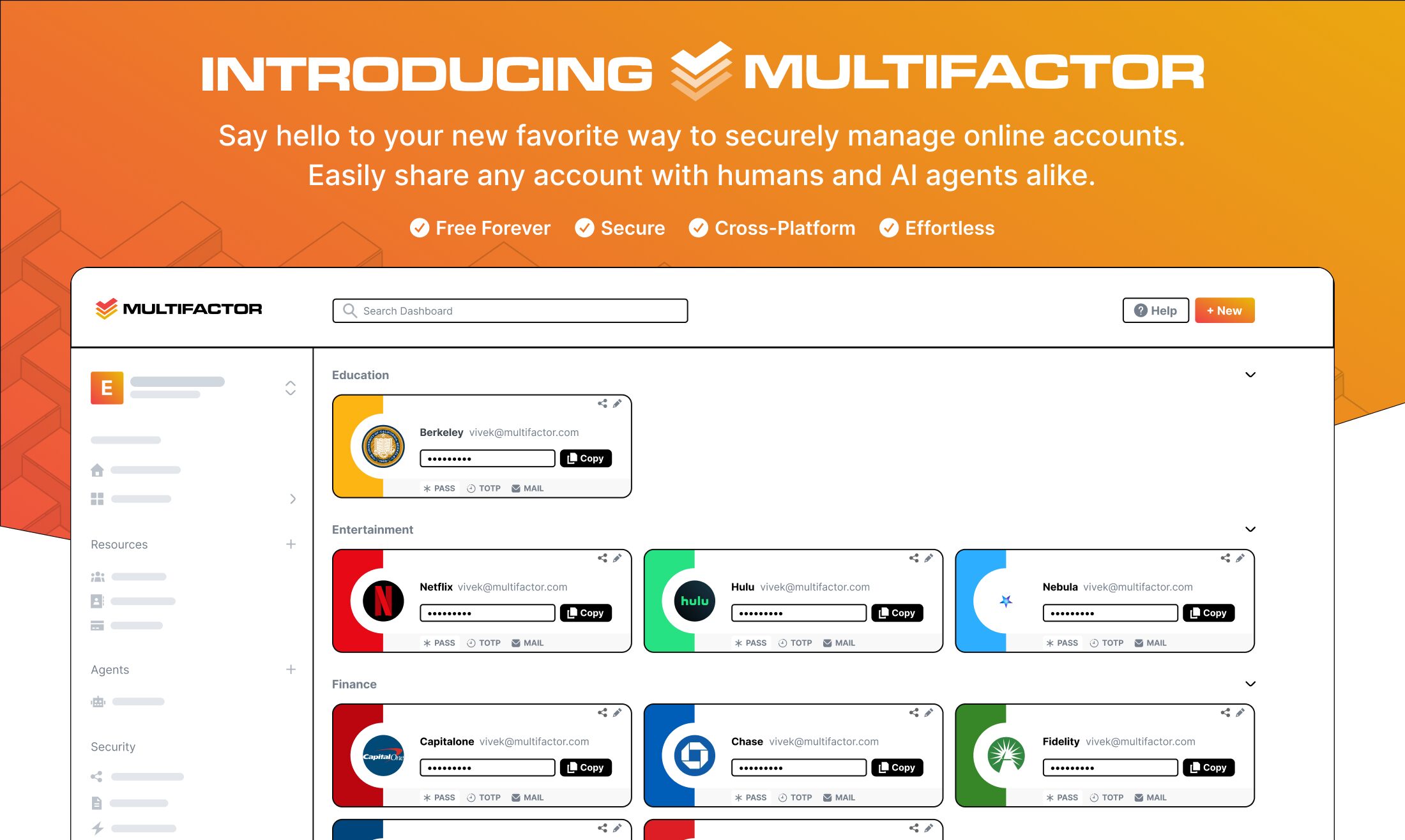
Multifactor represents a paradigm shift in account management and identity security for the agentic era. Unlike traditional password managers designed solely for credential storage, Multifactor enables secure, revocable account sharing with both humans and AI agents through innovative checkpoint link technology. The platform transforms any online account into a shareable resource as seamlessly as sharing a Google Doc, without ever exposing underlying passwords or authentication credentials.
Founded in 2025 by former CIA Officer Vivek Nair and NASA Scientist Colin Roberts, Multifactor has positioned itself as a Public Benefit Corporation committed to advancing cybersecurity through open-source innovation. The company addresses what the founders call the “AAA threat”—Authentication, Authorization, and Auditing vulnerabilities that emerge when deploying autonomous AI agents at scale.
Key Achievements and Milestones
Multifactor has achieved remarkable recognition despite its recent launch. The company was selected for Y Combinator’s Fall 2025 batch, one of the most competitive startup accelerators globally. Co-founder Vivek Nair received the prestigious Hertz Foundation Entrepreneurship Award through the Harold Newman and David Galas Entrepreneurial Initiative, providing non-dilutive funding and mentorship from the Hertz community. Additionally, Multifactor secured a Zcash Community Grant to support development of MFKDF2, demonstrating strong validation from both traditional venture capital and decentralized communities.
The company’s academic foundations are equally impressive. The original Multi-Factor Key Derivation Function research, published at USENIX Security 2023, won the Distinguished Artifact Award and has been cited extensively in academic literature. Vivek Nair earned his PhD from UC Berkeley at age 22 and previously received the CIA’s Exceptional Performance Award for extraordinary contributions to US national security. Colin Roberts brings deep expertise in mathematical cryptography from his work at NASA and prior crypto-focused startups.
Adoption Statistics
While specific customer numbers remain undisclosed at this early stage, Multifactor launched on Product Hunt in November 2025 and garnered over 437 upvotes with 73 community comments, indicating strong initial interest. The platform offers free forever access for individuals and small groups with unlimited accounts, passwords, and sharing capabilities across all devices. This freemium model positions Multifactor for rapid adoption among early adopters and technical users seeking alternatives to traditional password managers.
The company targets both consumer and enterprise markets. For consumers, Multifactor solves the growing problem of sharing accounts secured with passkeys, biometrics, and two-factor authentication—features that make modern accounts more secure but significantly harder to share safely. For enterprises, the platform provides the security infrastructure necessary for deploying AI agents with granular access controls, comprehensive audit trails, and instant revocation capabilities.
2. Impact and Evidence
Client Success Stories
Given Multifactor’s recent launch timeline, public case studies and formal customer testimonials are still emerging. However, the company has documented early success through its participation in Y Combinator, where rapid iteration and product-market fit validation are core methodologies. The platform’s value proposition addresses documented pain points in the password management and agentic AI security markets, both experiencing exponential growth.
Industry context supports Multifactor’s approach. The global password management market, valued at approximately 3.75 billion USD in 2025, is projected to reach 8.28 billion USD by 2029 with a compound annual growth rate of 21.9 percent. Simultaneously, non-human identities including AI agents are expected to exceed 45 billion by end of 2025—over twelve times the global workforce—with only 10 percent of executives reporting well-developed management strategies.
Performance Metrics and Benchmarks
Multifactor’s technical architecture delivers measurable performance advantages. The platform’s post-quantum cryptographic implementation using CRYSTALS-Kyber and CRYSTALS-Dilithium provides security against future quantum computing threats while maintaining client-side encryption speeds under 12 milliseconds of additional computational overhead in typical web browsers. This represents a significant improvement over traditional password-based key derivation functions.
The checkpoint link sharing mechanism enables instant access revocation without password resets—a critical advantage over conventional credential sharing methods. Traditional approaches require changing passwords and re-distributing new credentials to all authorized users, a process that can take hours or days and often results in outdated access persisting. Multifactor’s architecture ensures revocation takes effect immediately across all shared access points.
For AI agent deployments, Multifactor provides fine-grained permission controls enabling scenarios like granting an agent access to read email but not send messages, or view financial transactions but not initiate transfers. These capabilities directly address the authentication and authorization challenges identified by security researchers as the primary barriers to safe agentic automation at scale.
Third-Party Validations
The company’s technological foundation has received extensive academic validation. The original MFKDF research earned the Distinguished Artifact Award at USENIX Security 2023, one of the most prestigious computer security conferences globally. The work was co-authored with Professor Dawn Song of UC Berkeley, a renowned expert in computer security and artificial intelligence whose research group has produced numerous influential security technologies.
Independent security researchers and technology analysts have recognized Multifactor’s approach as addressing critical gaps in existing identity security solutions. The platform’s focus on zero-trust architecture aligns with National Institute of Standards and Technology guidelines and federal mandates for government agencies. The company’s commitment to open-source cryptographic primitives enables independent security audits and community verification of security claims.
Technology media coverage highlights Multifactor as pioneering what co-founder Vivek Nair calls “agentic security”—the next pillar of cybersecurity following cloud security. Publications including the Hertz Foundation, startup ecosystem platforms, and technology blogs have featured the company’s mission to enable secure collaboration between humans and AI agents without compromising credential security.
3. Technical Blueprint
System Architecture Overview
Multifactor employs a sophisticated zero-trust architecture built on three foundational pillars: client-side post-quantum encryption, secure checkpoint proxy technology, and distributed key management. The system ensures that actual credentials never transit networks or reside on Multifactor servers, even temporarily. Instead, authentication occurs through a trusted execution environment that acts as a secure intermediary between users and destination services.
The checkpoint link mechanism represents a novel approach to access delegation. When a user creates a checkpoint for an account, Multifactor generates a unique URL containing encrypted parameters that authorize temporary, revocable access according to specified permissions. Recipients authenticate to Multifactor, which then establishes a secure session with the destination service on their behalf using stored credentials that remain hidden throughout the process. This architecture resembles capabilities-based security models found in academic operating systems research but applied to web services and applications.
The Multi-Factor Key Derivation Function forms the cryptographic core of the platform. MFKDF expands traditional password-based key derivation by incorporating multiple authentication factors—including time-based one-time passwords, hardware tokens, biometrics, and passkeys—directly into the key derivation process. This provides exponential security improvements over single-factor approaches. For example, combining a 40-bit entropy password with a 20-bit entropy TOTP code yields 60 bits of combined entropy rather than simply the sum, because attackers must simultaneously guess all factors correctly due to the avalanche effect of the underlying cryptographic hash function.
API and SDK Integrations
While comprehensive developer documentation is still emerging given the company’s recent launch, Multifactor is designed with extensibility as a core principle. The platform supports one-click import from major password managers including LastPass, Apple Passwords, and Google Password Manager, enabling seamless migration for users with existing credential stores. This interoperability reflects the company’s commitment to providing practical solutions rather than forcing users to abandon established workflows.
For AI agent integration, Multifactor enables programmatic access through what the company describes as “secure account use” capabilities. AI systems can be granted access to specific account features through pre-configured permissions and natural language commands. The platform loads accounts in secure, isolated cloud browsers where actual credentials remain hidden from AI models and are never transmitted to third-party AI providers. This architecture prevents common vulnerabilities like prompt injection attacks from compromising user credentials.
The company’s open-source MFKDF2 and MFCHF2 libraries, currently under development with support from the Zcash Foundation, will provide developers with production-ready cryptographic primitives for implementing multi-factor authentication in their own applications. These Rust-based implementations are designed for high performance and security-critical applications including cryptocurrency wallets.
Scalability and Reliability Data
Multifactor’s architecture leverages modern cloud infrastructure to provide global availability and performance. The platform’s design separates the control plane—which manages user vaults, permissions, and audit logs—from the data plane that establishes actual authenticated sessions with destination services. This separation enables horizontal scaling to handle increasing user loads and account access requests.
The post-quantum cryptographic implementation demonstrates practical performance characteristics suitable for production deployment. Research indicates CRYSTALS-Kyber key encapsulation operations complete in milliseconds on standard hardware, while CRYSTALS-Dilithium digital signatures provide quantum-resistant authentication with reasonable computational overhead. These algorithms were selected by NIST as standards for post-quantum cryptography after rigorous evaluation of security properties and implementation efficiency.
As a newly launched platform, Multifactor has not yet published uptime statistics or service level agreements. However, the company’s technical leadership includes veterans from organizations with extremely high reliability requirements. Vivek Nair’s experience leading cyber operations for the CIA and DOD, combined with Colin Roberts’ background building mission-critical systems at NASA, provides strong foundations for engineering a robust and dependable platform.
4. Trust and Governance
Security Certifications
As an early-stage startup launched in 2025, Multifactor is in the process of pursuing formal security certifications. Industry-standard frameworks like SOC 2 Type 2 and ISO 27001 typically require 12 to 18 months of documented security practices before organizations can undergo formal audits. These certifications, while not yet completed, are standard expectations for enterprise-grade security platforms and likely represent key milestones on the company’s roadmap.
The platform’s security architecture incorporates best practices from established frameworks. Zero-trust principles align with NIST Special Publication 800-207 guidelines for zero trust architecture. The use of NIST-standardized post-quantum algorithms demonstrates commitment to compliance with federal cryptographic standards. The company’s Public Benefit Corporation status includes commitments to security and transparency as core organizational values rather than optional features.
Data Privacy Measures
Multifactor implements a zero-knowledge architecture where user data remains encrypted at all times with keys derived from user authentication factors. The company cannot access user credentials, passwords, or decrypted vault contents—a fundamental privacy protection built into the platform’s cryptographic design. This architecture means that even in worst-case scenarios like court orders or data breaches, Multifactor lacks the technical capability to expose user secrets.
The platform’s approach to AI agent security includes strong isolation guarantees. When AI systems access user accounts through Multifactor, the actual credentials and sensitive authentication factors remain shielded within secure execution environments. AI models receive only the data and capabilities explicitly authorized by permission policies, with all actions logged for auditability. This design prevents both malicious prompt injection attacks and unintended data exposure through AI system vulnerabilities.
Privacy protections extend to sharing scenarios. Checkpoint links can be configured with time limits, usage restrictions, and specific permission scopes. When access is revoked, previously shared users immediately lose all capabilities without requiring password changes or credential rotation. This granular control enables privacy-conscious sharing patterns impossible with traditional credential-sharing approaches.
Regulatory Compliance Details
Multifactor’s architecture addresses requirements across multiple regulatory frameworks. For organizations subject to GDPR, the platform’s zero-knowledge design inherently satisfies data minimization principles since Multifactor itself cannot access user data. The ability to instantly revoke access supports GDPR’s requirements for timely response to data subject requests and the right to be forgotten.
Healthcare organizations subject to HIPAA can leverage Multifactor’s audit trail capabilities to demonstrate proper access controls and monitoring. The platform logs every authentication event, permission grant, and access revocation with cryptographically signed records providing non-repudiation guarantees. These detailed logs support compliance audits and forensic investigations if security incidents occur.
Financial institutions facing regulatory requirements like SOC 2, PCI DSS, and various banking standards benefit from Multifactor’s fine-grained access controls. The ability to grant read-only access, restrict transaction capabilities, and implement time-limited access windows enables least-privilege security models required by financial regulations. The platform’s post-quantum cryptography also provides future-proofing against quantum computing threats that concern regulators focused on long-term data confidentiality.
5. Unique Capabilities
Checkpoint Link Technology
Multifactor’s signature innovation transforms how accounts are shared in the modern digital ecosystem. Traditional sharing methods require either revealing passwords completely—a security antipattern—or complex workarounds like creating separate sub-accounts with their own credentials. Checkpoint links eliminate these tradeoffs by creating time-limited, revocable access tokens that work with any online account regardless of whether the destination service has native sharing features.
The technical implementation separates the concept of “having credentials” from “being able to authenticate.” When a checkpoint link is created, Multifactor stores encrypted credentials in its secure vault and generates a capability token granting specific permissions. Recipients authenticate to Multifactor and present the capability token, which authorizes Multifactor to authenticate to the destination service on their behalf through a proxy architecture. The recipient never sees or possesses the underlying credentials, yet can interact with the account according to granted permissions.
This design enables sophisticated sharing scenarios. A family can share streaming service access where each member has their own Multifactor identity but uses the same underlying account. A business can grant contractors time-limited access to marketing tools without creating full employee accounts or sharing passwords via insecure channels. An AI agent can be authorized to process customer service emails but restricted from accessing administrative settings or user databases.
Multi-Factor Cryptographic Stack
The company’s foundational research in multi-factor cryptography represents a significant advance in practical key management. Traditional password-based systems suffer from the fundamental weakness that passwords alone rarely provide sufficient entropy to resist determined attackers. Adding authentication factors like two-factor codes improves security, but conventional implementations treat these factors as sequential checks rather than cryptographically combining their entropy.
MFKDF fundamentally changes this model by incorporating all authentication factors directly into key derivation. The system generates cryptographic keys by combining material from passwords, TOTP codes, hardware tokens, biometric factors, and other authentication methods. Because the key derivation process requires simultaneous knowledge of all factors, attacking the system becomes exponentially harder. A system using a 40-bit password and 20-bit TOTP provides 60 bits of combined security rather than being limited to the weaker 40-bit password alone.
The threshold MFKDF construction enables account recovery scenarios without sacrificing security. Users can configure policies like “any three of five factors” enabling recovery if they lose a device or forget a password, while maintaining strong protection against attackers who might compromise a single factor. This addresses a critical usability challenge in high-security systems where strict security often conflicts with practical recovery mechanisms.
Post-Quantum Security Architecture
Multifactor’s commitment to post-quantum cryptography positions the platform for long-term security against emerging quantum computing threats. Current public-key cryptographic systems like RSA and elliptic curve cryptography face existential risk from sufficiently powerful quantum computers using Shor’s algorithm. While such computers don’t yet exist, the “harvest now, decrypt later” threat is real—adversaries can capture encrypted data today and decrypt it once quantum computers become available.
The platform implements CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures, both selected by NIST as post-quantum cryptography standards in 2024. These lattice-based algorithms resist known quantum attacks while maintaining practical performance characteristics. The implementation approach emphasizes cryptographic agility—the ability to upgrade algorithms as standards evolve—ensuring the platform can adopt improved primitives as post-quantum cryptography matures.
For organizations with long-term data sensitivity, post-quantum protection isn’t optional—it’s essential. Medical records, financial documents, government secrets, and intellectual property all require confidentiality spanning decades. Multifactor’s architecture ensures that data encrypted today remains secure even after quantum computers capable of breaking current encryption become reality.
AI Agent Security Controls
The platform’s approach to AI agent authentication represents a novel solution to one of 2025’s most pressing cybersecurity challenges. As organizations deploy autonomous AI agents with increasing capabilities, traditional identity and access management systems prove inadequate. AI agents require continuous authentication, dynamic permission management, and granular action logging—capabilities rarely found in existing enterprise identity platforms.
Multifactor addresses these requirements through purpose-built agentic identity features. AI agents are provisioned with unique cryptographic identities rather than shared service accounts. Permission policies specify not just which accounts agents can access, but which specific actions within those accounts are authorized. An agent might read customer service emails but be prohibited from sending external communications, or view financial data while being unable to initiate transactions.
The secure browser environment isolates agent actions from underlying credentials and provides comprehensive logging of every interaction. Organizations can review audit trails showing exactly which data agents accessed, what actions they performed, and whether any attempted actions were blocked by permission policies. These capabilities enable safe deployment of agentic automation while maintaining security controls and compliance with regulatory requirements.
6. Adoption Pathways
Integration Workflow
Multifactor is designed for minimal friction during adoption. Individual users can begin using the platform by downloading browser extensions, desktop applications, or mobile apps available for all major platforms including Windows, macOS, Linux, Android, and iOS. The initial setup process guides users through creating their secure vault with a master password and optional additional authentication factors.
Importing existing credentials from other password managers occurs through one-click import functionality supporting LastPass, Apple Passwords, and Google Password Manager. The import process transfers encrypted credentials directly into the Multifactor vault while maintaining security throughout the migration. Users can retain their previous password manager during a transition period, gradually shifting to Multifactor as comfort and confidence develop.
For organizations deploying Multifactor at scale, the platform supports enterprise provisioning workflows. IT administrators can create organizational vaults, define permission policies, and provision users according to role-based access control models. Integration with existing identity providers through standard protocols enables single sign-on experiences where employees authenticate once and gain access to both Multifactor-managed credentials and other corporate resources.
AI agent integration follows a similar pattern of progressive enhancement. Organizations begin by storing credentials for services AI agents need to access within Multifactor vaults. Agents are provisioned with API credentials and permission policies defining authorized actions. The agent code integrates with Multifactor APIs to request access, which triggers secure authentication to destination services through the checkpoint proxy architecture.
Customization Options
The platform provides flexibility to accommodate diverse use cases and security requirements. Users can configure vault encryption with varying levels of additional authentication factors beyond master passwords. Organizations with heightened security needs might require hardware security keys, biometric authentication, or multiple time-based codes, while users prioritizing convenience might rely primarily on passwords with optional two-factor authentication.
Checkpoint link creation offers extensive customization of sharing parameters. Links can be configured as single-use or multi-use, with absolute expiration times or relative durations like 24 hours from creation. Permission scopes range from full account access equivalent to having the password, to narrow capabilities like read-only access or specific feature restrictions. Sharing recipients can be authenticated Multifactor users or anonymous parties accessing via the link alone, with different security tradeoffs appropriate for different scenarios.
For enterprises, policy customization enables enforcement of organizational security standards. Administrators can mandate minimum authentication factor requirements, restrict which types of accounts can be shared externally, define maximum checkpoint link durations, and require approval workflows before sensitive accounts are delegated to AI agents. These policy controls balance security with usability according to organizational risk tolerance.
Onboarding and Support Channels
As a newly launched platform backed by Y Combinator, Multifactor is building its support infrastructure alongside product development. The company maintains a blog with technical deep-dives explaining cryptographic innovations, security architecture decisions, and practical use cases. This educational content helps users understand not just how to use the platform, but why Multifactor’s approach offers security advantages over conventional password managers.
Community engagement occurs through Product Hunt, Reddit discussions, and social media presence. Early adopters share experiences, identify edge cases, and suggest feature enhancements through these channels. The company’s open-source commitment extends to its cryptographic libraries, where developer communities can examine code, propose improvements, and verify security claims through independent audits.
Enterprise customers likely receive dedicated onboarding support as part of commercial agreements, though specific support tier details are not yet publicly documented. The company’s technical leadership brings experience from organizations with demanding users—CIA operations, NASA missions, and crypto wallet security—suggesting strong appreciation for the importance of reliable support when security is paramount.
7. Use Case Portfolio
Enterprise Implementations
Multifactor addresses several critical enterprise scenarios that traditional password managers handle inadequately. Marketing teams frequently need to share access to social media accounts, advertising platforms, and content management systems with agencies, contractors, and temporary staff. Conventional approaches require either sharing passwords insecurely or creating numerous sub-accounts with complex permission management. Multifactor enables instant provisioning of time-limited access with specific capability restrictions, then instant revocation when projects complete.
Financial operations teams face similar challenges when granting accountants, auditors, or temporary CFOs access to banking portals, payment processors, and financial software. The ability to grant read-only access for statement review while preventing transaction initiation provides security controls previously requiring extensive custom development or manual oversight. Audit trails documenting every access and action support compliance requirements and forensic investigations.
Customer support teams increasingly deploy AI agents to handle routine inquiries, but safely connecting these agents to customer databases, CRM systems, and internal knowledge bases poses significant security risks. Multifactor provides the authentication and authorization infrastructure enabling granular control over which customer data agents can access, what actions they can perform, and comprehensive logging of all agent activities. Organizations can deploy agentic automation while maintaining security controls required for regulatory compliance.
Academic and Research Deployments
Research institutions face unique credential management challenges. Labs commonly share access to computational resources, scientific instruments, research databases, and cloud platforms among faculty, graduate students, postdocs, and visiting researchers. The fluid nature of academic teams—with members joining and leaving on semester rhythms and grant cycles—creates constant pressure on IT departments managing access provisioning and deprovisioning.
Multifactor’s checkpoint link architecture maps naturally to academic collaboration patterns. Principal investigators can grant time-limited access to cloud computing resources for the duration of a research project, with automatic expiration when grants end. Shared equipment reservations can integrate with Multifactor to enforce access controls ensuring only authorized researchers operate expensive instruments. Visiting scholars gain temporary access to relevant resources without requiring full institutional account provisioning.
The platform’s post-quantum security also addresses long-term data protection needs in academic research. Scientific datasets, genomic information, and longitudinal studies often remain sensitive for decades. Ensuring this data remains confidential against future quantum computing threats aligns with research integrity and ethical obligations to study participants.
ROI Assessments
Enterprise password manager deployments typically emphasize security risk reduction rather than direct cost savings, making ROI calculations focus on avoided losses rather than revenue generation. However, several quantifiable benefits support business case development. IT support ticket reduction represents measurable savings—password reset requests constitute significant helpdesk volume. Systems enabling self-service recovery through multi-factor authentication reduce support costs while improving user experience.
Security incident costs provide the most substantial ROI justification. Data breaches from compromised credentials average millions of dollars in remediation, legal, regulatory, and reputational costs. Organizations can quantify risk reduction by calculating breach probability times expected impact, then demonstrating how improved credential security reduces these risks. Multifactor’s instant revocation capability particularly reduces costs associated with offboarding employees or contractors, where delayed access removal creates windows of vulnerability.
Operational efficiency gains from streamlined credential sharing represent another ROI component. When teams can instantly provision time-limited access rather than scheduling IT tickets and waiting for manual account creation, project velocity increases. The ability to grant specific permissions without full account access reduces the security review overhead often required before provisioning broad access rights.
8. Balanced Analysis
Strengths with Evidential Support
Multifactor’s fundamental architecture provides several compelling advantages over conventional password managers. The zero-knowledge design with client-side encryption ensures user data remains private even from Multifactor itself, addressing legitimate concerns about trusting third-party services with sensitive credentials. The post-quantum cryptographic implementation demonstrates forward-thinking engineering, protecting against threats that will emerge as quantum computing matures.
The checkpoint link innovation represents genuine progress in solving the credential sharing problem. By separating authentication capability from credential possession, the platform enables secure sharing patterns impossible with traditional approaches. The instant revocation property eliminates security windows where former employees or contractors retain access after offboarding—a persistent challenge in enterprise environments.
The company’s leadership combines exceptional credentials and relevant experience. Vivek Nair’s background in CIA cyber operations, academic achievements including youngest-ever UC Berkeley PhD in computer science, and recognition through the Hertz Fellowship and Distinguished Artifact Award at USENIX Security demonstrate both technical excellence and security expertise. Colin Roberts’ mathematical rigor from his NASA background and crypto startup experience complements this with deep cryptographic knowledge.
The platform’s open-source commitment to fundamental cryptographic primitives enables community verification and independent security audits. Publishing MFKDF and MFCHF as open-source libraries rather than keeping them proprietary demonstrates confidence in the security of the constructions and commitment to advancing the field rather than merely building a commercial product.
Limitations and Mitigation Strategies
As a newly launched platform, Multifactor faces the classic challenge of building trust in security-critical infrastructure. Users must trust that the company’s zero-knowledge architecture is correctly implemented, that no backdoors exist, and that the cryptographic design actually provides claimed security properties. While the leadership’s credentials and academic publications support these claims, independent security audits from reputable firms would strengthen confidence.
The checkpoint proxy architecture requires ongoing operational security. While users’ credentials remain encrypted, Multifactor’s infrastructure must reliably maintain the trusted execution environments where authentication occurs on users’ behalf. Any compromise of these systems could potentially expose credentials in transit even if vault storage remains secure. The company’s security practices, infrastructure hardening, and incident response capabilities will be critical to maintaining trust.
Competition from established password managers represents a significant business challenge. Products like 1Password, Bitwarden, LastPass, and Dashlane have years of development, extensive feature sets, large user bases, and established brand recognition. Multifactor’s innovative sharing and AI agent features differentiate the platform, but convincing users to migrate from familiar tools requires compelling advantages beyond incremental improvements.
The reliance on relatively new post-quantum cryptographic algorithms introduces potential risks. While CRYSTALS-Kyber and CRYSTALS-Dilithium underwent rigorous NIST evaluation, they lack the decades of scrutiny applied to current cryptographic standards. Undiscovered vulnerabilities remain possible, though cryptographic agility in the platform design enables algorithm updates if weaknesses emerge.
Enterprise adoption requires achieving security certifications like SOC 2 and ISO 27001, building integrations with identity providers and enterprise security tools, and developing sales and support infrastructure. As an early-stage startup, these capabilities are still maturing. Organizations with strict vendor requirements may need to wait until Multifactor achieves enterprise-readiness milestones.
9. Transparent Pricing
Plan Tiers and Cost Breakdown
Multifactor adopts a freemium business model designed to maximize adoption while building a sustainable enterprise business. The Consumer plan is free forever with unlimited accounts, unlimited passwords, unlimited sharing with friends and family, and availability across all devices. This generous free tier removes barriers to entry and enables widespread experimentation with the platform’s core capabilities.
The pricing model emphasizes that fundamental security should be accessible to everyone, not reserved for those willing to pay. This philosophy aligns with the company’s Public Benefit Corporation status and commitment to advancing cybersecurity for societal benefit. The free tier includes the same core security architecture—zero-knowledge encryption, post-quantum cryptography, and checkpoint link sharing—as paid offerings.
Enterprise pricing follows a custom quotation model typical of B2B security platforms. Organizations receive tailored proposals based on user count, required features, and integration needs. Enterprise plans include advanced auditing and compliance capabilities, priority customer support with service level agreements, and integrations with cloud role-based access control and single sign-on systems. This custom pricing approach enables flexibility for organizations with varying scales and requirements.
The contrast with major competitors highlights Multifactor’s value positioning. 1Password charges 2.99 USD per user monthly for individuals and 7.99 USD per user monthly for families. Enterprise pricing typically ranges from 7.99 to 14.99 USD per user monthly depending on tier. Bitwarden offers a free plan for individuals plus Premium at 0.83 USD monthly, with enterprise plans from approximately 3 to 6 USD per user monthly. LastPass provides free individual plans but charges 3 USD monthly for Premium and 4 USD per user monthly for business plans.
Total Cost of Ownership Projections
Evaluating total cost of ownership requires considering both direct subscription fees and indirect costs including migration, training, support, and opportunity costs of features not supported. For individual users and small teams, Multifactor’s free tier delivers zero direct costs while providing equivalent or superior functionality to paid competitors. The primary investment is time spent migrating from existing password managers, typically measured in hours rather than substantial financial outlay.
Enterprise deployments involve more complex TCO analysis. Direct licensing costs based on per-user monthly fees multiply across hundreds or thousands of employees, making cost per user a significant factor. However, indirect costs often dominate—IT staff time for deployment and integration, end-user training and support tickets, and opportunity costs from security incidents that occur due to inadequate credential management.
Multifactor’s instant revocation capability reduces the hidden costs associated with credential lifecycle management. Traditional approaches require manual tracking of which credentials need changing when team members leave, creating either labor-intensive password rotation processes or security risks from delayed revocation. Automated, instant revocation eliminates these tradeoffs, though quantifying this benefit requires measuring current costs of manual credential management in specific organizations.
Security incident cost avoidance represents the largest potential TCO component. Credential compromise causes the majority of security breaches, with average costs in the millions of dollars when including investigation, remediation, regulatory fines, legal costs, and reputation damage. Organizations can model TCO by estimating breach probability reduction and multiplying by expected breach costs, though these calculations involve substantial uncertainty.
10. Market Positioning
Competitor Comparison
The password management market includes numerous established players with different strengths and positioning. Direct comparison illuminates where Multifactor differentiates and where it faces challenges displacing incumbents.
| Feature | Multifactor | 1Password | Bitwarden | LastPass |
|---|---|---|---|---|
| Pricing | Free (Consumer), Custom (Enterprise) | $2.99-14.99/user/month | Free-$6/user/month | Free-$4/user/month |
| Open Source | Core crypto libraries | No | Fully open source | No |
| Checkpoint Sharing | Yes – core feature | Limited sharing | Password sharing | Password sharing |
| AI Agent Support | Yes – purpose-built | No | No | No |
| Post-Quantum Crypto | Yes – CRYSTALS | Standard encryption | Standard encryption | Standard encryption |
| Instant Revocation | Yes | Requires password change | Requires password change | Requires password change |
| Fine-Grained Permissions | Yes | Limited | Limited | Limited |
| Zero-Knowledge Architecture | Yes | Yes | Yes | Yes |
| Security Audits | Pending (new platform) | Regular audits | Regular audits | Regular audits |
| Enterprise SSO | Custom integration | Yes | Yes | Yes |
| Audit Trails | Comprehensive with cryptographic signatures | Yes | Yes | Yes |
| Platform Support | Windows, Mac, Linux, iOS, Android | Windows, Mac, Linux, iOS, Android | Windows, Mac, Linux, iOS, Android | Windows, Mac, Linux, iOS, Android |
Unique Differentiators
Several features distinguish Multifactor from established competitors. The checkpoint link architecture enabling seamless account sharing without exposing credentials represents the most significant differentiation. While other password managers support sharing vault entries containing passwords, recipients still see and possess the actual credentials. Multifactor’s approach genuinely separates access capability from credential knowledge.
Purpose-built AI agent support addresses an emerging market need that traditional password managers largely ignore. As organizations deploy autonomous AI systems requiring authenticated access to business applications, conventional credential management approaches prove inadequate. Multifactor’s granular permission controls, secure browser isolation, and comprehensive audit logging specifically target this use case.
Post-quantum cryptographic implementation demonstrates technical leadership and forward-thinking security engineering. While quantum computers capable of breaking current encryption don’t yet exist, the “harvest now, decrypt later” threat is real for data requiring long-term confidentiality. Organizations handling medical records, financial data, government secrets, or intellectual property benefit from quantum-resistant protection today.
The company’s public benefit corporation structure and open-source commitment to core cryptographic primitives differentiate Multifactor philosophically from purely commercial competitors. Users concerned about vendor lock-in, proprietary cryptography, or conflicts between profit maximization and security best practices may find this positioning compelling.
11. Leadership Profile
Bios Highlighting Expertise and Awards
Vivek Nair, Co-Founder and CEO, brings extraordinary credentials combining government service, academic excellence, and entrepreneurial vision. He served as a Technical Lead within elite cyber units of the US Central Intelligence Agency and Department of Defense, receiving the CIA’s Exceptional Performance Award for extraordinary contributions to US national security. This recognition acknowledges work advancing the frontiers of US cyber operations at the highest classification levels.
Nair’s academic achievements are equally impressive. He became the youngest-ever recipient of bachelor’s and master’s degrees in computer science from the University of Illinois Urbana-Champaign at ages 18 and 19 respectively. He completed his PhD in Computer Science at UC Berkeley at age 22, supported by prestigious fellowships from the National Science Foundation, National Physical Sciences Consortium, and Hertz Foundation. His doctoral research under Professor Dawn Song focused on applied cryptography and usable security.
Beyond government and academic work, Nair has authored numerous patents and patent applications for secure user authentication technologies. His research has been published at top-tier academic conferences including USENIX Security, ACM CHI, ACM UIST, and IEEE EuroS&P. Media including The Washington Post, Forbes, and Bloomberg have featured his work. The Hertz Foundation selected him for the 2025 Entrepreneurship Award recognizing Multifactor’s mission to redefine identity security for the agentic era.
Colin Roberts, Co-Founder and CTO, contributes deep mathematical and cryptographic expertise. He holds a PhD in Mathematics with specialization in applied cryptography and previously worked as a NASA scientist designing robust and provably secure mission-critical multi-agent systems. His background emphasizes mathematical rigor and formal verification techniques ensuring security properties hold under precise threat models.
Roberts brings startup experience from prior roles at crypto-focused companies where he led engineering teams and architected scalable cryptographic systems. His technical approach combines pure mathematics with practical engineering, building production systems with formal security proofs rather than relying solely on implementation best practices. This methodology aligns with Multifactor’s mission to deliver cryptographically provable security properties.
The complementary expertise of the founding team—Nair’s operational security experience and user-centric design background combined with Roberts’ mathematical cryptography and systems engineering—provides a strong foundation. Both founders demonstrate commitment to advancing cybersecurity through both commercial product development and open-source research contributions.
Patent Filings and Publications
The intellectual property portfolio underlying Multifactor spans both traditional patents and open-source academic publications. Nair has filed numerous patent applications covering secure authentication techniques, multi-factor key derivation methods, and user-centric security protocols developed during his academic research and government service. These patents protect commercial applications of the underlying innovations while enabling open-source implementations for non-commercial use.
The academic publication record demonstrates rigorous peer review and independent validation of security claims. The USENIX Security 2023 paper “Multi-Factor Key Derivation Function for Fast, Flexible, Secure, and Practical Key Management” by Nair and Song won the Distinguished Artifact Award, recognizing exceptional quality in reproducible research artifacts. This work has been cited extensively in subsequent academic literature on authentication and key management.
Additional publications include research on virtual reality privacy and security, biometric authentication in immersive environments, and secure multi-party computation for blockchain applications. The breadth of research topics reflects the founders’ wide-ranging expertise in modern security challenges spanning consumer applications, enterprise systems, and emerging technologies like AI and extended reality.
The company’s commitment to publishing open-source implementations of core cryptographic primitives—MFKDF, MFCHF, and upcoming MFKDF2—distinguishes Multifactor from competitors relying entirely on proprietary cryptography. This transparency enables independent security audits and allows the broader security community to adopt and improve the underlying techniques.
12. Community and Endorsements
Industry Partnerships
Multifactor’s participation in Y Combinator Fall 2025 cohort connects the company with an extensive network of successful startups, investors, and mentors. Y Combinator alumni include Airbnb, Stripe, Dropbox, Reddit, Coinbase, and numerous other technology giants. This network provides both immediate support during product development and long-term strategic relationships as the company scales.
The Hertz Foundation community represents another valuable partnership network. Hertz Fellows include multiple Nobel Prize winners, MacArthur Fellows, National Medal of Science recipients, and founders of successful technology companies. The entrepreneurship award provides not just funding but mentorship from experienced entrepreneurs who have successfully built startups in related fields.
The Zcash Foundation grant supporting MFKDF2 development connects Multifactor to the cryptocurrency and blockchain communities. These ecosystems prioritize security and cryptographic innovation, providing demanding users who will stress-test the platform and contribute valuable feedback. The open-source nature of blockchain communities also aligns with Multifactor’s commitment to transparent cryptography and community-driven security validation.
Academic partnerships through UC Berkeley and collaborative research with Professor Dawn Song’s research group provide ongoing access to cutting-edge security research and talent pipelines. These relationships enable Multifactor to recruit exceptional engineers and cryptographers while staying current with emerging security threats and defensive techniques.
Media Mentions and Awards
Technology media coverage of Multifactor emphasizes the company’s novel approach to long-standing security challenges. The Product Hunt launch generated significant attention with over 437 upvotes and extensive discussion of the checkpoint link concept. Technology blogs and startup ecosystem publications have featured the company’s mission to enable secure AI agent deployment.
The Hertz Foundation’s announcement of Nair’s entrepreneurship award brought attention from scientific and technology communities, highlighting Multifactor as addressing the emerging “agentic security” category that Nair describes as the next pillar of cybersecurity after cloud security. This positioning frames the company not as an incremental improvement to password managers but as pioneering a new security category.
LinkedIn discussions and social media coverage from technology leaders and security professionals indicate growing awareness of the challenges Multifactor addresses. Posts highlighting the risks of unsecured AI agents, the inadequacy of traditional credential management for autonomous systems, and the need for new identity security paradigms create favorable context for Multifactor’s value proposition.
While comprehensive media coverage typically emerges as startups mature beyond initial launch, Multifactor’s academic foundations and high-profile founders have generated early attention unusual for seed-stage companies. The combination of government credentials, academic achievements, and Y Combinator participation positions the company for increasing visibility as product development progresses and customer adoption grows.
13. Strategic Outlook
Future Roadmap and Innovations
While specific product roadmap details remain proprietary, public statements and technical foundations indicate several likely development priorities. Achieving enterprise-readiness milestones including SOC 2 Type 2 and ISO 27001 certifications will be essential for selling to large organizations with strict vendor requirements. These certifications typically require 12 to 18 months of documented security practices and formal audits.
Expanding integrations with enterprise identity providers, single sign-on systems, and security information and event management platforms will be critical for enterprise adoption. Organizations expect password managers to integrate seamlessly with existing IT infrastructure rather than requiring wholesale changes to identity architectures. Partnerships with major identity vendors could accelerate these integrations.
The open-source cryptographic library development—MFKDF2, MFCHF2, and related primitives—represents ongoing work supported by the Zcash Foundation grant. Releasing production-ready implementations in Rust will enable broader adoption of multi-factor key derivation beyond Multifactor’s own platform, potentially establishing these techniques as industry standards. This aligns with the public benefit mission of advancing cybersecurity broadly rather than merely building proprietary technology.
AI agent security features likely represent a key differentiation area as agentic automation adoption accelerates. Enhanced permission policy languages, integration with emerging standards like Model Context Protocol, and purpose-built monitoring and auditing tools for AI agent behavior could establish Multifactor as the de facto identity infrastructure for autonomous systems. This positioning could prove highly valuable as industry analysts predict non-human identities will outnumber human identities fifty to one by 2026.
Market Trends and Recommendations
Several converging trends create favorable market conditions for Multifactor’s growth. The global password management market is experiencing robust expansion with compound annual growth rates between 15 and 22 percent across multiple analyst reports. This growth is driven by increasing cybersecurity awareness, regulatory compliance requirements, and the proliferation of online accounts requiring credential management.
The agentic AI revolution represents a potentially transformative market opportunity. Organizations are deploying autonomous AI systems faster than security infrastructure can adapt, creating documented vulnerabilities and compliance concerns. Gartner predicts that 25 percent of security breaches in 2025 will involve AI agent abuse. This threat landscape creates urgent demand for identity and access management solutions specifically designed for autonomous systems.
Post-quantum cryptography adoption is accelerating due to NIST standardization and federal mandates requiring migration to quantum-resistant algorithms by 2030. Organizations with long-term data sensitivity cannot afford to wait, creating market demand for solutions implementing post-quantum cryptography today. Multifactor’s early adoption provides competitive advantage as this trend accelerates.
The shift toward zero-trust architecture in enterprise security creates favorable conditions for platforms built on zero-trust principles from inception. Organizations replacing perimeter-based security models with continuous verification and least-privilege access need identity infrastructure that supports these paradigms. Multifactor’s zero-knowledge architecture and fine-grained permission controls align naturally with zero-trust requirements.
Recommendations for potential adopters vary by category. Individual users and small teams should evaluate Multifactor’s free tier as a modern alternative to traditional password managers, particularly if account sharing is a frequent need. The checkpoint link approach elegantly solves sharing scenarios that are awkward or insecure with conventional tools.
Enterprise organizations should consider Multifactor as strategic infrastructure for AI agent deployments. As autonomous systems become more prevalent in business processes, identity and access management becomes critical security infrastructure. Organizations planning significant agentic automation should evaluate whether traditional identity platforms adequately address AI agent security requirements or whether purpose-built solutions provide necessary capabilities.
Organizations in highly regulated industries or handling data requiring long-term confidentiality should assess the importance of post-quantum cryptography in their security architecture. While quantum computers capable of breaking current encryption don’t yet exist, the harvest-now-decrypt-later threat is real. Adopting quantum-resistant encryption today provides protection against future threats.
Final Thoughts
Multifactor represents an ambitious attempt to reimagine identity security for an era defined by AI agents, quantum computing threats, and ubiquitous account sharing needs. The platform’s technical foundations—post-quantum cryptography, multi-factor key derivation, and checkpoint link architecture—demonstrate genuine innovation addressing real problems inadequately solved by existing password managers.
The founding team’s exceptional credentials combining government intelligence experience, academic research excellence, and entrepreneurial vision provide strong foundations for executing a complex technical and business challenge. Recognition from prestigious institutions including Y Combinator, the Hertz Foundation, and USENIX Security validates both the technology and the market opportunity.
However, succeeding in the competitive password management market requires more than technical excellence. Multifactor must build trust as security-critical infrastructure, achieve necessary certifications, develop enterprise features and integrations, and convince users to migrate from established alternatives. These challenges are substantial for any startup, even one with remarkable founders and innovative technology.
The company’s timing may prove fortuitous. The agentic AI revolution is creating urgent demand for identity infrastructure specifically designed for autonomous systems—a category where traditional password managers are not well positioned. If Multifactor can establish itself as the de facto identity platform for AI agents while simultaneously serving as an excellent password manager for humans, the total addressable market expands dramatically beyond existing password management boundaries.
For organizations evaluating Multifactor, the decision framework should consider both immediate needs and strategic positioning. The platform delivers genuine value today for account sharing use cases, particularly in scenarios requiring fine-grained permissions and instant revocation. The free tier enables risk-free experimentation to evaluate fit.
The more strategic consideration involves the role of AI agents in future operations. Organizations planning significant autonomous system deployments should carefully evaluate whether existing identity infrastructure adequately addresses agentic security requirements. Multifactor’s purpose-built features for AI agent authentication, authorization, and auditing may prove essential as autonomous systems become more prevalent and security risks become more apparent.
Ultimately, Multifactor’s success will depend on execution—building a reliable platform, achieving enterprise certifications, developing necessary integrations, and scaling both technology and organization. The foundations are strong, the timing appears favorable, and the team has demonstrated ability to tackle complex challenges. The market will determine whether these advantages translate into sustainable competitive position in a crowded but rapidly growing category.